How to Fix and Prevent a WordPress Phishing Attack [3 Easy Steps]
A WordPress Phishing Attack is one of the most common WordPress attacks that costs businesses billions of dollars each year.
According to AWPG (Anti-Phishing Working Group) data, in 2023 alone, the number of unique phishing sites (attacks) reached a staggering 5 million, greater than the 4.7 million phishing attacks in 2022.
Therefore, as a website owner, protecting your WordPress site from phishing attacks is crucial for maintaining its security and credibility.
But don’t worry! In this comprehensive guide, we will explore exactly what is a phishing attack, how to identify phishing attacks, and most importantly, how to effectively fix and prevent it in 3 simple steps.
Ready? Let’s dive right in!
What is a WordPress phishing attack?
A WordPress phishing attack, also called a WordPress phishing hack, occurs when a hacker creates a replica of a legitimate WordPress login page to trick users into entering their credentials. Once the hacker got the credentials, they could access the website without authorization.
Simply put, a phishing attack is about having official-looking pages on your website that trick people into sharing private information.
Check out these phishing attack examples that appear to be from popular brands.
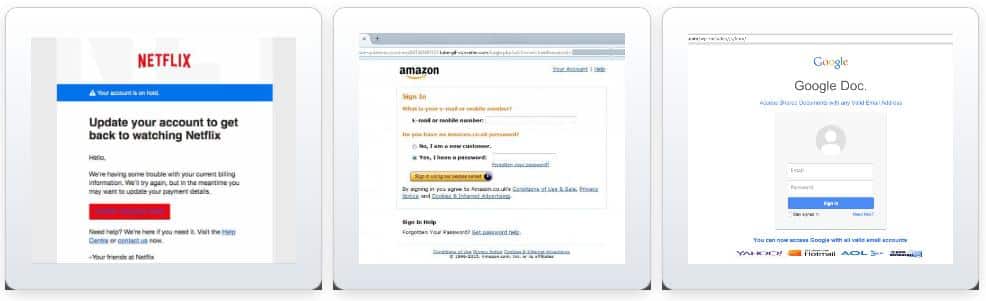
A phishing attack is extremely harmful to your WordPress site. If the malware stays on your site, you could face serious consequences. Google might flag your site, which negatively affects your SEO and traffic.
Also, users could avoid visiting your site because they think it’s unsafe, which could lead to loss of customers.
How to Identify a WordPress Phishing Attack
Recognizing the signs of a WordPress phishing attack early on is imperative for minimizing potential damage. When you see Google’s warnings, such as “this website has been identified as a phishing site,” you might be concerned about the security of your website.
If you are wondering how to check a phishing website, then here are some key indicators to watch for a WordPress phishing attack:
- Visit Flagged URLs: Try visiting the URLs that Google has flagged, but do it from a different computer, network, or incognito mode. Sometimes, hackers hide malware from website administrators, so checking from different sources is important.
- Google Search Console: Go to Google Search Console and look for Security Issues notices. This will tell you if there’s any deceptive content on your site that Google has detected.
- Suspicious Emails: Be wary of emails that claim urgent action is required on your WordPress site. These emails often contain unfamiliar links or attachments that may lead to phishing pages.
- Unusual Pages or Posts: Look for any strange or unrelated pages or posts on your website. While this can be tricky, phishing pages might appear in your sitemap or site files.
- Unusual Login Attempts: These may indicate a WordPress Brute Force Attack. Be sure to monitor your WordPress login history for any unauthorized login attempts or unfamiliar IP addresses, and immediately investigate any suspicious activity.
- Favicons of Known Brands: Hackers often impersonate well-known brands, so they might use real brand logos on their phishing pages. Check your site files for any familiar brand logos that shouldn’t be there.
- Look for Third-Party Links/Ads: Ads on your website can sometimes contain phishing campaigns. Refresh your website several times to see the different ads. Even if an ad has nothing to do with your site’s content, it could still contain deceptive material or a link.
If Google Search Console shows security issues, it’s likely your website is a victim of a WordPress phishing attack, and you should proceed with removing the phishing content.
3 Easy Steps to Remove the WordPress Phishing Attack
Removing a WordPress phishing attack requires more than just simply scanning your website with malware scanners such as Sucuri or Wordfence. It often requires a manual and careful approach.
So, if you want to know how to remove phishing attacks, check out the following three simple steps that will help you detect and remove phishing attacks from your WordPress site:
Step 1: Check for Suspicious Directories in Your Website’s Root
Phishing attacks on WordPress sites are often hidden in separate folders within the main website directory. Attackers typically upload phishing pages as compressed files, like .zip archives.
So, if you suspect a phishing attack, follow the steps below to check your website’s root directory for unfamiliar archive files or suspicious folders.
#1: Access Your Website’s Root Directory
- Log in to your web hosting account or use an FTP client to access your website’s files.
- Navigate to your WordPress website’s root directory. This is typically where files like “index.php” and “wp-config.php” are located.
#2: Look for Archive Files or Unfamiliar Folders
- Scan through the files in the root directory.
- Look for any archive files (such as .zip) that you do not recognize.
- Check for folders with suspicious names that do not relate to your legitimate website content.
- Pay attention to any folders that seem out of place or contain files unrelated to your site’s usual content.
#3: Check for Extracted Phishing Files
- If you find an archive file, extract its contents to see what’s inside.
- Look for HTML or PHP files, CSS stylesheets, and images that are not part of your website’s original design.
- Check these files for phishing content, such as fake login pages or forms requesting sensitive information.
- Remove any suspicious files or folders that you find.
Step 2: Review wp-content, Plugins, and Theme Folders
Sometimes, attackers use more sophisticated methods to hide phishing attacks. They might place them in the wp-content directory or within specific plugin and theme folders.
Follow the steps below to review each of them individually.
#1: Navigate to the wp-content Directory
- Within your website’s root directory, locate the “wp-content” folder.
- Open the “wp-content” folder to access themes, plugins, and other content-related files.
#2: Examine Plugin and Theme Folders
- Open the “plugins” folder within “wp-content.”
- Check each plugin folder for files that seem unusual or out of place.
- Look for files with unfamiliar names or extensions, especially within plugin folders.
- Repeat the same process for the “themes” folder within “wp-content,” examining each theme folder for suspicious files.
#3: Verify File Integrity
- Compare the files within the plugin and theme folders to the original versions.
- Check the WordPress.org repository or official sources for the plugins and themes you use.
- Delete any files that do not match the original or seem suspicious.
Step 3: Scan for Malicious Redirects
Besides uploading phishing pages, hackers can include malicious redirects in legitimate files as well. These redirects can send your visitors to fraudulent content without their knowledge.
To check each malicious redirect thoroughly, follow the steps below:
#1: Inspect Core Files for Redirects
- Open the “.htaccess” file in the root directory of your WordPress site.
- Look for any unusual code that redirects users to external or phishing pages.
- Remove any suspicious redirect rules from the “.htaccess” file.
#2: Check the Main index.php File
- Locate the “index.php” file in the root directory.
- Review the contents of the “index.php” file for any injected scripts or suspicious code.
- Remove any unauthorized code that could lead to malicious redirects.
#3: Review the “wp_options” Table in the Database
- Access your WordPress database using a tool like phpMyAdmin.
- Look for the “wp_options” table, which stores various site settings.
- Review the entries in the “wp_options” table for any suspicious URLs or redirect rules.
- Delete any entries that do not belong or seem suspicious.
#4: Consider Using Security Plugins
- Install a reputable WordPress security plugin such as Sucuri or Wordfence.
- Run a malware scan using the security plugin to detect and remove any remaining traces of phishing attacks.
- Follow the recommendations provided by the security plugin to enhance your site’s security.
By following these three steps and carefully examining your WordPress files and directories, you can identify and remove any traces of a phishing attack on your website.
Remember, to carry out these steps effectively, you must have a solid understanding of WordPress and its components.
Most Common Types of Phishing Attacks in WordPress
Phishing attacks can impact WordPress users in two main ways. Firstly, your WordPress site itself could be compromised, either by hackers using it to target others or by administrators receiving phishing emails.
Let’s discuss each type of WordPress phishing attack in detail:
1. WordPress Phishing Pages
Attackers often use a WordPress site as a platform to distribute malware through phishing. They hide malicious pages on your website, making them hard to detect. These pages often look like legitimate parts of your site, tricking visitors into providing sensitive information.
As an administrator, you might not realize these pages exist until someone reports receiving a phishing email.
2. WordPress Phishing Emails
As a WordPress site administrator, you might receive phishing emails designed to look like familiar notifications. These emails can easily deceive even experienced users. Hackers even forward emails to make them seem like they’re from a trusted source.
Before clicking any links in the email, you should ask these questions:
- Do I recognize the sender?
- Is the link going to a legitimate URL, or could it be a redirection hack?
To stay safe:
- Always question emails that seem suspicious, even if they look familiar.
- Before clicking on any links, perform a quick search or verify with known contacts.
- Remember, even the most experienced WordPress users can fall victim to well-crafted phishing emails.
Awareness of these common types of phishing attacks in WordPress can help you stay vigilant and protect your website and sensitive information from potential threats.
How to Prevent Phishing Attacks for WordPress
Malware gets into WordPress due to security weaknesses in plugin or theme code. Hackers target these vulnerabilities to access your site and insert harmful code without your knowledge. Often, website administrators only realize the breach when it’s too late, leading to significant damage and loss.
Because of this, prevention is critical to protecting your WordPress site from phishing attacks. Here are five effective prevention measures that you can implement right away:
- Remove Non-Authorized Users: Regularly audit and remove any unauthorized users or accounts from your WordPress site. Limiting access helps reduce the risk of unauthorized access and potential phishing attempts.
- Update Your Website Regularly: Stay vigilant with WordPress updates, including core files, themes, and plugins. Updates often include critical security patches that protect against known vulnerabilities exploited by hackers.
- Use Strong Login Credentials: Always use strong, unique passwords for your WordPress admin accounts. Avoid using common passwords or easily guessable combinations. Consider employing a password manager to generate and securely store complex passwords.
- Install a Reputable Security Plugin: Security plugins such as Sucuri, Wordfence, or MalCare offer real-time monitoring, malware scanning, and firewall protection. These plugins fortify your WordPress site against attacks and provide alerts for suspicious activity.
- Install an SSL Certificate: An SSL (Secure Sockets Layer) certificate encrypts data exchanged between your website and users’ browsers. This encryption enhances security and establishes trust with visitors, reducing the risk of phishing attacks.
Wrapping Up
A WordPress phishing attack poses a significant threat to your website’s security and integrity. Hopefully, by following the steps outlined in this guide, you have effectively identified, removed, and prevented your WordPress site from potential phishing attacks.
If you want to protect your WordPress content, check out the Password Protected plugin. It allows you to password protect WordPress pages, posts, categories, WooCommerce shop pages, and even entire WordPress sites with a single password.
Lastly, if you encounter difficulty, contact our team of WordPress experts so we can help you with the WordPress phishing attack.
Thank you for reading. Stay safe!
Frequently Asked Questions
What are the 3 most common types of phishing attacks?
The three most common phishing attacks are email phishing, credential harvesting, and malware downloads. In each case, the goal is to trick the user into disclosing sensitive information.
Why is my WordPress site flagged as phishing?
If your WordPress site contains suspicious links, emails, or files that look like phishing attempts, it might get flagged as phishing. Regular security checks and updates can help resolve this issue.
How do I check if my website has phishing?
You can check the website for phishing by monitoring suspicious activities, conducting malware scans, and using security tools (security plugins) to detect phishing content.
What is an example of a WordPress phishing attack?
An example of a WordPress phishing attack is receiving an email that appears to be from your WordPress site, asking you to log in urgently. The email includes a link to a fake login page that steals your credentials when you enter them.

