WordPress Brute Force Attack: 4 Easy Ways to Prevent It in 2024
A WordPress brute force attack is one of the most commonly used WordPress attacks that hackers attempt to gain access to your website.
According to WPHackedHelp, around 40 million brute force attacks are happening every day across the globe.
As WordPress is one of the most widely used CMS (Content Management Systems) for creating websites, it is likely that millions of WordPress sites are also subject to brute-force attacks on a daily basis.
Fortunately, there are some easy and effective ways to prevent a brute-force attack on your WordPress site. In today’s blog post, we will explain what a brute force attack is, how to stop a brute force attack, and what you should avoid for brute force attack mitigation.
Let’s jump right in!
What is a Brute Force Attack in WordPress?
A brute force WordPress attack is a type of cyberattack in which the hacker tries to gain access to your wp-admin or any password protected screen using trial and error to guess the password and username.
Hackers use automated bots or scripts that attempt to log in to your WordPress site by entering different usernames and passwords, usually from a list of common or stolen ones. They do this repeatedly until they succeed or until they reach a limit.
A brute force attack can be very dangerous for your WordPress site. If hackers get access to your site through a brute force attack, they can easily:
- Overload your server and slow down your site performance
- Lock you out of your site by exceeding the number of login attempts
- Access your admin dashboard and make changes to your site settings, content, or plugins
- Install malware or backdoors on your site that can compromise your security and privacy
- Steal your personal or financial information or your users’ data
Therefore, preventing brute force attacks on your WordPress site and keeping your login credentials secure is essential.
However, by default, WordPress does not provide extra protection against brute force attacks; there are precautions you can take to prevent this.
How to Prevent Brute Force Attack on a WordPress Site [4 Easy Ways]
There are several ways to stop a brute force attack on your WordPress site, but we will focus on four easy and effective ones that you can implement right away, which include:
- Adding Two-Factor Authentication (2FA)
- Creating a Strong and Unique Password
- Disabling XML-RPC WordPress file
- Enforcing Limit Login Attempts
Let’s look at each of these methods in more detail.
Method #1: Enable Two-Factor Authentication (2FA)
Usually, when you sign in to a WordPress site by just entering a username and password, you use a single-step authentication method. The good news is that you can make authentication (login process) more secure by adding a second step, also known as two-step or two-factor authentication.
In simple terms, two-factor authentication (2FA) is a security feature that adds an extra layer of protection to your login process. It requires you to verify your WordPress login credentials (username and password) along with a second factor, such as a code sent to your phone or email, a push notification, or an app.
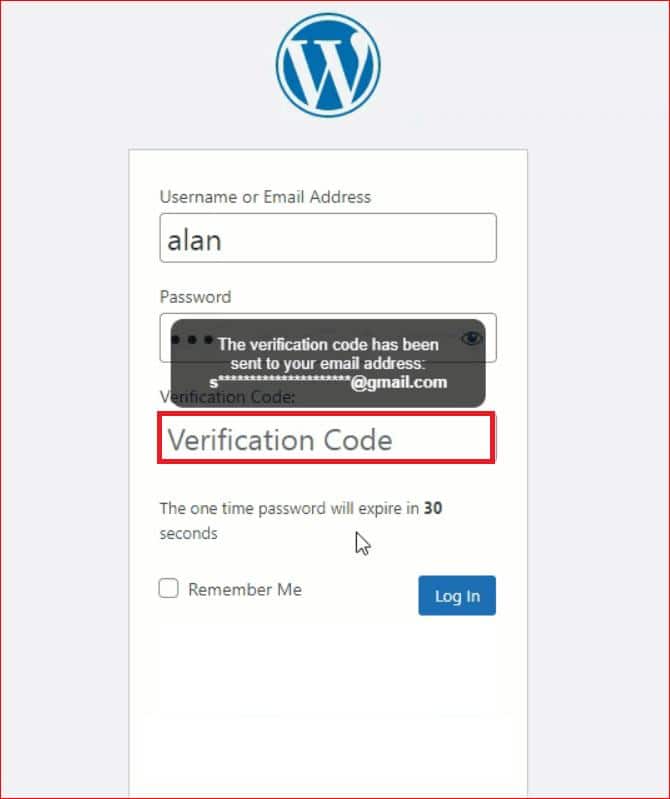
This way, even if a hacker manages to guess your password, they won’t be able to access your site without the second factor.
To enable 2FA on your WordPress site, you can use a plugin such as miniOrange’s Google Authenticator, which offers various options for verification, such as OTP over SMS and email, authentication code via all major All-TOTP Authenticator Apps like Google Authenticator, Microsoft Authenticator and more.
Additionally, you can customize the settings to suit your preferences, such as enabling 2FA for specific user roles, setting the time limit for verification, or choosing the backup methods.
Method #2: Make Your Password Strong & Unique
The biggest problem in WordPress brute force attack mitigation is often the user themselves and how they choose their passwords. Passwords are a major weakness in brute force protection because people tend to use easy-to-remember passwords and use the same ones for different accounts.
Hackers use botnets (which are like networks of robots) to try lots of different passwords, hoping to get access. To make it harder for them, make sure you have a password that is unique and has a mix of numbers and letters.
To create a strong password, it should be:
- Between ten and 50 characters long.
- Contain both big and small letters.
- Include numbers and special characters.
- Different from passwords you use for other accounts or websites
To change your WordPress password, click Users → Profile from the right-hand menu. Then, find the “Account Management” section and select “Set New Password.”
WordPress will suggest a strong password (which is very hard to remember), but you can also make your own.
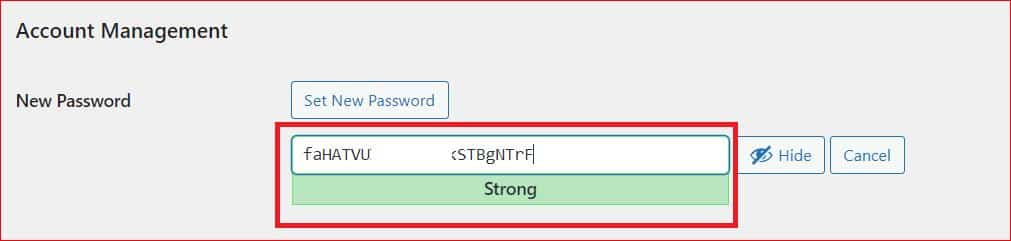
We suggest you create a strong password that you can remember, as WordPress will show you how strong or weak your new password is as you type it.
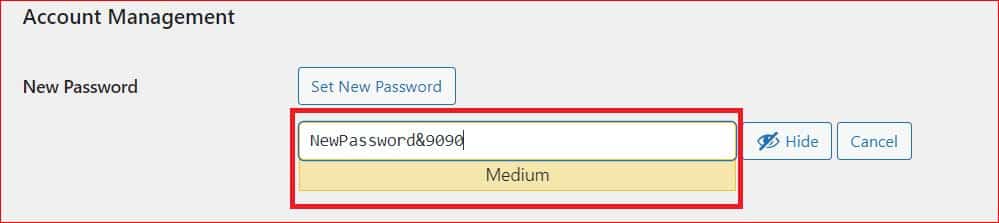
Moreover, for an even more secure and random password, you can use a tool like LastPass to generate one with a mix of uppercase and lowercase letters, numbers, and symbols. Once you have your new password, paste it in the text box and click Update Profile at the bottom of the page to save your changes.
NOTE: For extra safety against hacking attempts, changing your WordPress password every three to four months is a good idea.
Method #3: Disable XML-RPC File in WordPress
XML-RPC (XML for Xtensible Markup Language and RPC for Remote Procedure Call) describes a set of rules in WordPress that enables remote communication between your site and other applications, such as mobile apps, pingbacks, or trackbacks.
However, hackers can also use it to launch brute force attacks on your WordPress site, as it allows them to send multiple requests to your site with one HTTP request. This means that they can try thousands of passwords in a short time without triggering any limit or alert.
In WordPress version 3.5, XML-RPC is enabled by default. In some cases, it is useful for developers, but for most of us, keeping it enabled can introduce vulnerabilities.
To disable an XML-RPC file on your WordPress site, use a plugin called Disable XML-RPC, which blocks all XML-RPC requests to your site with one click.
Alternatively, you can manually disable XML-RPC by adding the following code to your .htaccess file in your WordPress root directory:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
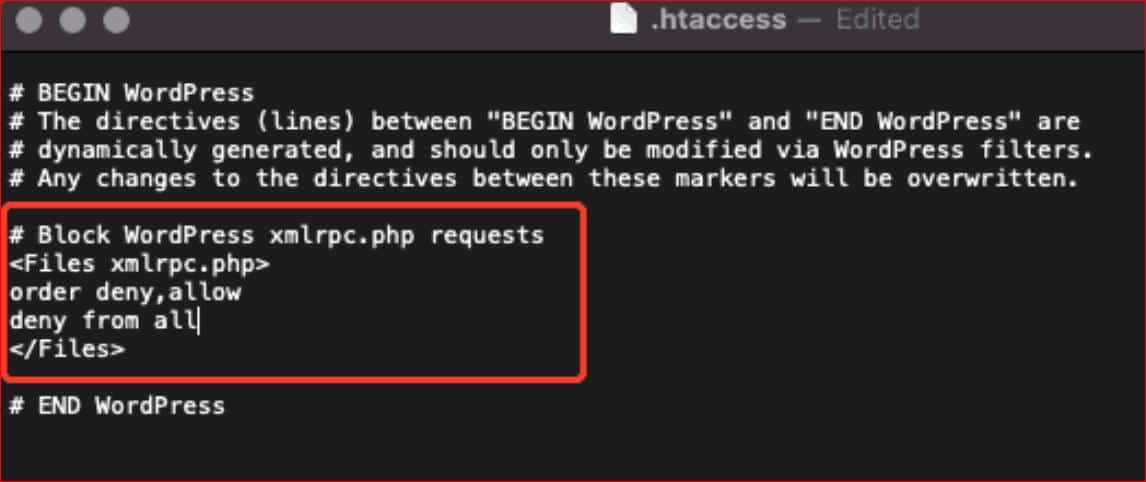
Using this piece of code, you can restrict all XML-RPC requests in WordPress. If you want to allow a particular IP address, then replace the “deny from all” line of code with “allow from xxx.xxx.xxx.xxx”
WARNING: Disabling XML-RPC might affect some WordPress functionalities or third-party plugins. Therefore, you should check first if you need XML-RPC for a particular feature before disabling it.
Method #4: Implement Limit Login Attempts
Another way to stop a brute force attack on your WordPress site is to implement a limit on the number of login attempts that a user can make within a certain time period.
By default, WordPress allows unlimited login attempts. That’s why it’s one of the most effective methods to block hackers from trying too many passwords and locking them out of your site.
Additionally, by limiting login attempts, you can prevent excessive server resource consumption by bots, as they cannot attempt to log in more than your defined limit.
To implement limit login attempts on your WordPress site, you can use a plugin called Limit Login Attempts Reloaded, which allows you to customize the settings, such as the number of allowed retries, the lockout duration, the Auto Deny of malicious IP addresses, email notifications and much more.

For WordPress Content Protection:
If you want to protect your password protected site against brute force attacks, then use the limit login feature of the password protected plugin, which allows you to limit the number of attempts a single user can make in a certain period.
Things You Should Avoid to Prevent Brute Force Attack
Besides the methods we mentioned above, there are also some things you should avoid to prevent a brute force attack on your WordPress site, such as:
- Using ‘admin’ as Your Username: This is the default username in older versions of WordPress, and it is the first one that hackers try. So, changing it to something harder to guess would be a good idea.
- Same Password for Multiple Sites or Accounts: You increase the risk of having your password exposed or stolen from another hacked site when you use the same password for multiple sites or accounts. Make sure you use a different password for every site you use, especially for your WordPress site.
- Ignoring WordPress Updates: WordPress releases regular updates that fix bugs, improve performance, and enhance security. Always keep your WordPress core, themes, and plugins to the latest version, as they may contain patches for vulnerabilities that hackers can exploit.
Final Thoughts on Brute Force Attack Mitigation
WordPress brute force attack is a common and serious threat to any WordPress site, yet you can prevent it with a few easy steps. By enabling 2FA, making your password strong and unique, disabling XML-RPC, and implementing limit login attempts, you can protect your site from unauthorized access and keep your data and users safe.
Additionally, suppose you want to protect your password protected WordPress content from a brute force attack. In that case, we highly recommend using the Password Protected plugin, as it allows you to set limited login attempts for your password protected screen, which restricts hackers after certain failed attempts.
Lastly, if you have any questions or suggestions, please feel free to contact us via our support channels. We would love to hear from you.
Frequently Asked Questions
Is WordPress safe from brute force login attempts?
WordPress is quite secure but not immune to brute force login attempts. Yet you can prevent your WordPress site from brute force attacks by following some best practices, such as using a strong and unique password, implementing two-factor authentication, enforcing limit login attempts, and disabling XML-RPC.
Which WordPress plugin helps defend against brute force attacks?
There are many WordPress plugins that can help you defend against brute force attacks, but some of the most popular and effective ones are Sucuri, Jetpack, Limit Login Attempts Reloaded, and Password Protected Plugin.
How long can a password be against brute force?
The length of a password against brute force depends on the complexity and randomness of the password, as well as the strength and speed of the brute force attack. However, some general guidelines suggest that a password should be at least 8 characters long, and preferably 12 or more, to resist brute force attacks.
What is an example of a brute force attack?
An example of a brute force attack is when a hacker tries to log in to your WordPress site by using a list of common or stolen usernames and passwords, such as ‘admin’, ‘123456’, ‘password,’ etc. Mostly, they use automated software or bots to try different combinations until they find the right one.

